Complete IT Offboarding Checklist for Tech Teams in 2026
When an employee leaves, their devices, credentials, and data don’t automatically leave with them, unless your offboarding process ensures it.
In hybrid, cloud-driven workplaces, IT offboarding is no longer a simple HR step; it’s a vital part of maintaining data security, compliance, and sustainability. Every retired laptop, phone, or server carries both risk and value: risk if sensitive information isn’t completely erased, and value if its components can be recovered, reused, or recycled responsibly.
An updated, consistent offboarding process doesn’t just protect data; it also supports a company’s environmental and governance goals by ensuring technology is handled with care throughout its entire lifecycle.
That’s where 4THBIN comes in.
For more than a decade, we’ve helped organizations close this loop through certified data destruction, RemoteReturn mail-back programs, and IT asset disposition and recovery (ITAD) solutions.
In this blog, we’ll walk you through the complete IT offboarding process for 2026, exploring how automation, compliance, and sustainability come together to create a future-ready strategy for responsible technology management.
Why IT Offboarding Needs a Structured Approach
Improper IT offboarding remains one of the most common sources of data risk. Research shows that 48% of data breaches stem from unrevoked credentials or unmanaged devices, a gap that’s entirely preventable.
Without structure, organizations face:
- Data exposure: Forgotten drives or accounts leave sensitive data vulnerable.
- Compliance lapses: Missing certificates can lead to audit penalties.
- Environmental waste: Devices disposed of improperly add to the growing e-waste challenge.
A structured IT offboarding process ensures consistency, accountability, and measurable progress toward sustainability and data protection goals.
Your Complete IT Offboarding Checklist
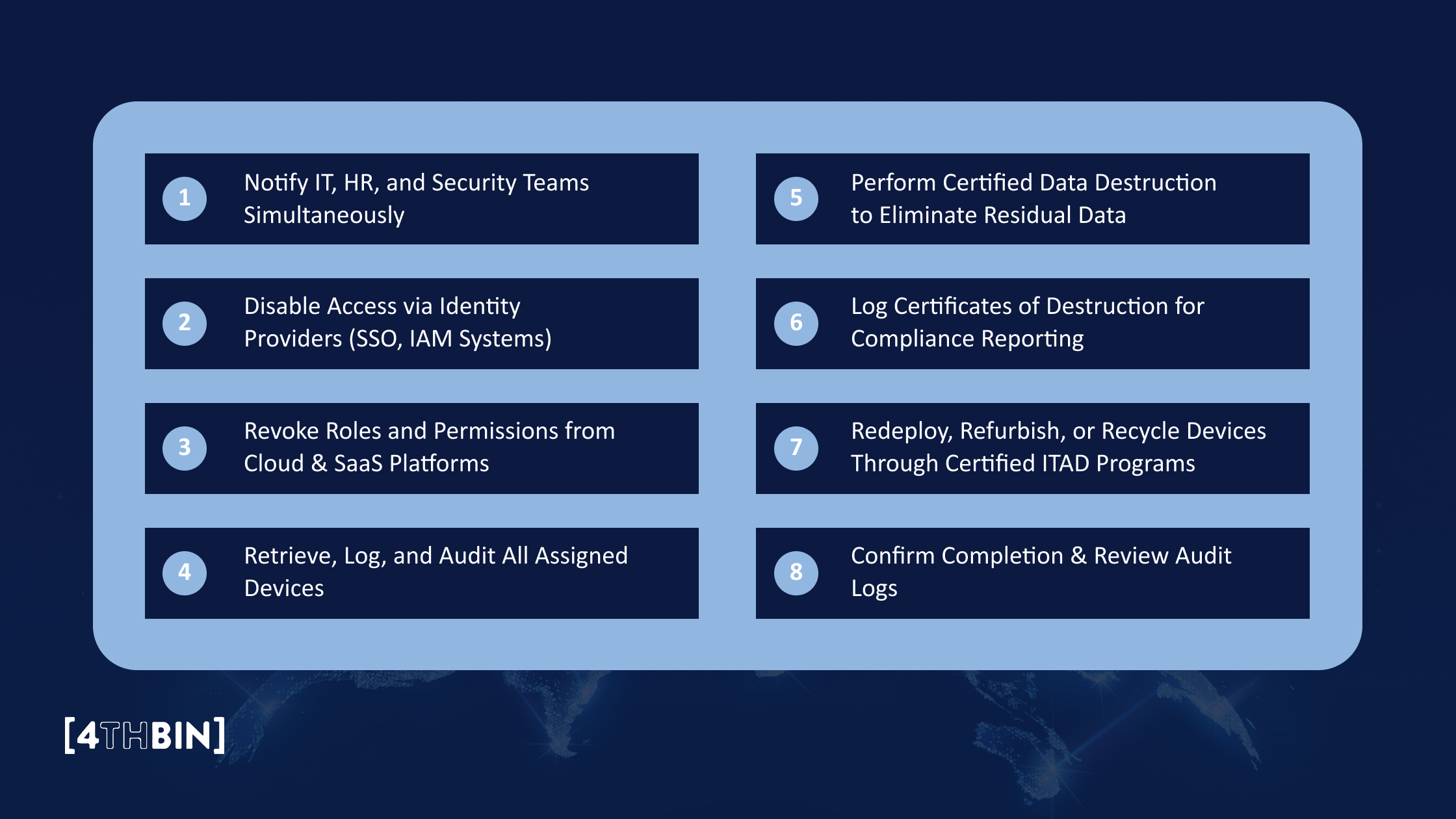
A strong IT offboarding process isn’t just about ticking boxes; it’s about protecting sensitive data, meeting compliance requirements, and ensuring technology is handled responsibly. Here’s a detailed breakdown of each step your tech team should include:
1. Notify IT, HR, and Security Teams Simultaneously
Offboarding starts with coordination. As soon as an employee's departure is confirmed, HR, IT, and Security must be notified simultaneously to initiate a synchronized workflow. Early notification prevents delays in access termination and asset collection, two key points where data risks often emerge.
A connected process ensures that identity deprovisioning, device retrieval, and compliance documentation happen concurrently, not in isolation.
2. Disable Access via Identity Providers (SSO, IAM Systems)
Identity management systems (like Okta, Azure AD, or Google Workspace) should be the first line of defense. Immediate access revocation through SSO and IAM tools prevents unauthorized entry into corporate systems and sensitive data repositories.
Automating this step ensures credentials, tokens, and shared logins are disabled instantly, reducing the window for potential data misuse.
3. Revoke Roles and Permissions from Cloud & SaaS Platforms
Many organizations overlook the deeper layers of access, such as administrative roles within AWS, GitHub, Jira, or Salesforce. These permissions often persist beyond account disablement, leaving behind “ghost” access points.
A comprehensive revocation process removes user roles and shared credentials across all integrated platforms, ensuring there are no backdoors into company data or systems.
4. Retrieve, Log, and Audit All Assigned Devices
Every device, from laptops to smartphones to external drives, must be physically or digitally accounted for. Tracking serial numbers, conditions, and ownership ensures that no hardware with sensitive data remains unmonitored.
Using digital asset tracking (barcodes or RFID) allows IT teams to log devices in real-time and create an auditable chain of custody, a key compliance requirement for organizations managing remote or hybrid teams.
5. Perform Certified Data Destruction to Eliminate Residual Data
Simply deleting files or reformatting drives doesn’t make data disappear. Certified data destruction ensures the complete and irreversible erasure of data, meeting compliance frameworks such as GDPR, HIPAA, and NIST 800-88.
At 4THBIN, our certified data destruction services guarantee that every device is wiped, verified, and securely processed, eliminating the risk of residual data exposure while maintaining full regulatory compliance.
6. Log Certificates of Destruction for Compliance Reporting
After data destruction, it’s fundamental to generate and store proof of compliance. Certificates of destruction (CoD) verify that devices were processed securely and in accordance with industry standards.
These reports serve as audit-ready documentation, a safeguard against potential compliance inquiries, and a powerful addition to ESG and sustainability disclosures.
7. Redeploy, Refurbish, or Recycle Devices Through Certified ITAD Programs
Not all retired devices are waste. Many can be refurbished, reused, or responsibly recycled. Partnering with a certified IT asset disposition (ITAD) provider, such as 4THBIN, ensures that valuable components are recovered while reducing landfill impact.
This step not only minimizes e-waste but also contributes to measurable sustainability metrics, including reduced greenhouse gas emissions and resource conservation, which are vital for corporate ESG goals.
8. Confirm Completion & Review Audit Logs
Finally, close the loop. Review system logs, access records, and ITAD documentation to confirm that all revocations, data wipes, and recycling actions have been completed.
An internal audit helps identify any gaps in your process, ensuring each offboarding instance meets your organization’s security, compliance, and environmental standards.
How Automation Strengthens Offboarding?
Manual offboarding processes are often slow and prone to errors. Automation streamlines this process by connecting HR systems, identity platforms, and ITAD workflows into one cohesive system.
Automated ITAD and offboarding systems help:
- Track devices in real time using barcodes or RFID tags.
- Erase and verify data automatically through certified destruction software.
- Generate compliance documentation instantly for audits and ESG reporting.
Industry insights reveal that automation-driven ITAD programs significantly enhance tracking accuracy and compliance efficiency, demonstrating that automation serves as both a data protection tool and a sustainability enabler.
How to Successfully Implement Automation in ITAD Operations
Transitioning to automated ITAD processes takes planning, coordination, and the right mindset. A phased and informed approach ensures your organization gains the full benefits of automation, without disrupting existing workflows or compromising compliance.
1. Start with Process Mapping
Before introducing automation tools, it’s crucial to thoroughly understand your current workflows. Map every stage of your ITAD process, from asset intake and tracking to data destruction and compliance reporting.
Identify repetitive, manual, or error-prone tasks such as spreadsheet-based inventory logging, certificate generation, or approval routing. These are prime candidates for automation.
By visualizing where time is lost or where human error is most likely to occur, you can target automation efforts that deliver immediate impact. For example, automating device tracking through barcode or RFID scanning not only reduces human error but also provides real-time visibility into the status of every asset.
A clear process map also serves as a communication tool, helping stakeholders see how automation fits into the bigger picture of secure, sustainable IT asset management.
2. Adopt Gradual Integration
Automation doesn’t have to happen all at once, and in most cases, it shouldn’t. Introduce automation tools in phases, starting with high-impact, low-risk areas. For instance, begin with automated certificate generation or digital logging of device intake before expanding to data destruction verification and compliance reporting.
This phased rollout enables your team to test functionality, identify bottlenecks, and refine workflows before scaling up. It minimizes operational disruption, helps manage budgets more effectively, and ensures a smoother transition for all departments involved.
Gradual integration also provides a continuous learning curve, helping your teams build confidence in the system, adapt to new tools, and recognize measurable performance gains over time.
3. Train and Align Teams
Automation is only as effective as the people who use it. That’s why successful adoption depends on clear communication and consistent training. Engage IT, compliance, and sustainability teams from the beginning so they understand not only how automation works, but why it matters.
Training should cover both the technical aspects, such as using automation dashboards or monitoring audit logs, and the strategic elements, including how automation supports compliance frameworks (GDPR, HIPAA, R2v3) and ESG reporting.
Encourage collaboration across departments to break silos: IT ensures technical accuracy, compliance teams validate standards, and sustainability leads translate data into measurable impact metrics. When everyone understands their role in the process, automation becomes an enabler of shared goals, security, transparency, and environmental accountability.
When implemented thoughtfully, automation doesn’t replace human oversight; it amplifies it. By combining process visibility, phased adoption, and team alignment, organizations can enhance the resilience, verifiability, and future-readiness of their ITAD operations.
Make Your Offboarding Secure & Highly Effective with 4THBIN
As organizations manage growing digital footprints across hybrid environments, every departing employee represents both a security risk and an opportunity to reinforce responsible technology management.
At 4THBIN, we help companies transform this process from a checklist into a secure, compliant, and sustainable framework. By combining automation with certified e-recycling and comprehensive reporting, we ensure your IT offboarding is efficient, transparent, and fully aligned with environmental and data security standards.
Our certified data destruction services eliminate residual data risks by ensuring every device is wiped, verified, and documented for audit readiness. Meanwhile, our IT asset disposition and recovery (ITAD) programs are devised to maximize value recovery and minimize electronic waste (e-waste), helping organizations close the loop between data protection and sustainability.
Partner with 4THBIN to build a future-ready offboarding strategy!











